Hello Friends, Today I am Telling you About OSI (Open Systems Interconnection) Model
What Is the OSI (Open Systems Interconnection) Model?
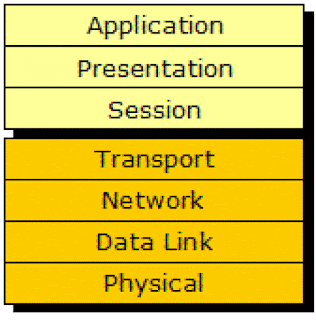
Layers of the OSI Model.
Definition: The OSI model defines internetworking in terms of a vertical stack of seven layers. Upper layers of the OSI model represent software that implements network services like encryption and connection management. Lower layers of the OSI model implement more primitive, hardware-oriented functions like routing, addressing, and flow control.
Data communication in the OSI model starts with the top layer of the stack at the sending side, travels down the stack to the sender's lowest (bottom) layer, then traverses the physical network connection to the bottom layer on the receiving side, and up its OSI model stack.
The OSI model was introduced in 1984. Designed to be an abstract model and teaching tool, the OSI model remains a useful for learning about today's popular network technologies like Ethernet and protocols like IP.
Examples: Internet Protocol (IP) corresponds to the Network layer of the OSI model, layer three. TCP and UDP correspond to OSI model layer four, the Transport layer. Lower layers of the OSI model are represented by technologies like Ethernet. Higher layers of the OSI model are represented by application protocols like TCP and UDP.
OSI 7 Layers:
The Open Systems Interconnection (OSI) model is a product of the Open Systems Interconnection effort at the International Organization for Standardization. It is a prescription of characterizing and standardizing the functions of a communications system in terms of abstraction layers
Application Layer:
The top, or seventh, layer of the OSI model is the Application layer. Contrary to what its name implies, the Application layer does not include software applications, such as Microsoft Word or Firefox. Instead, Application layer services facilitate communication between software applications and lower layer network services so that the network can interpret an application’s request and, in turn, the application can interpret data sent from the network.
Through Application layer protocols, software applications negotiate their formatting, procedural, security, synchronization, and other requirements with the network.
For example, when you choose to open a Web page in Firefox, an Application layer protocol called HTTP (Hypertext Transfer Protocol) formats and sends your request from your client’s browser (a software application) to the server. It also formats and sends the Web server’s response back to your client’s browser.
Suppose you choose to view the Exhibits page at the Library of Congress’s Web site. You type
“www.loc.gov/index.html” in Firefox and press Enter. At that point, Firefox’s API (application program interface), a set of routines that make up part of the software, transfers your request to the HTTP protocol. HTTP prompts lower layer protocols to establish a connection between your computer and the Web server. Next, HTTP formats your request for the Web page and sends the request to the Web server. One part of the HTTP request includes a command that begins with “GET” and tells the server what page you want to retrieve. Other parts of the request indicate what version of HTTP you’re using, what types of graphics and what language your browser can accept, and what browser version you’re using, among other things.
After receiving your computer’s HTTP request, the Web server responsible for http://www.loc.gov (http://www.loc.gov) responds, also via HTTP. Its response includes the text and graphics that make up the Web page, plus specifications for the content contained in the page, the HTTP version used, the type of HTTP response, and the length of the page. However, if the Web page is unavailable, the host, http://www.loc.gov (http://www.loc.gov), sends an HTTP response containing an error message, such as “Error
404 – File Not Found.”
After receiving the Web server’s response, your workstation uses HTTP to interpret this response so that Firefox can present the http://www.loc.gov/index.html (http://www.loc.gov/index.html ) Web page in a format you’ll recognize, with neatly arranged text and images. Note that the information issued by one node’s HTTP protocol is designed to be interpreted by the other node’s HTTP protocol.
However, as you will learn in later sections, HTTP requests cannot traverse the network without the assistance of lower layer protocols.
Presentation Layer:
Protocols at the Presentation layer accept Application layer data and format it so that one type of application and host can understand data from another type of application and host.
In other words, the Presentation layer serves as a translator. If you have spent any time working with computer graphics, you have probably heard of the GIF, JPG, and TIFF methods of compressing and encoding graphics. MPEG and QuickTime are two popular methods of compressing and encoding audio and video data. The popular audio format MP3, for example, uses MPEG compression. It can turn a music track that would require 30 MB of space on a CD into a file no larger than 3 MB – or even smaller, if lower quality were acceptable. Two well-known methods of encoding text are ASCII and EBCDIC. In each of these examples, it is the Presentation layer protocols that perform the coding and compression.
They also interpret coded and compressed formats in data received from other computers.
In the previous example of requesting a Web page, the Presentation layer protocols would interpret the JPG files transmitted within the Web server’s HTTP response.
Presentation layer services also manage data encryption (such as the scrambling of passwords) and decryption. For example, if you look up your bank account status via the Internet, you are using a secure connection, and Presentation layer protocols will encrypt your account data before it is transmitted. On your end of the network, the Presentation layer will decrypt the data as it is received.
Session Layer:
Among the Session layer’s functions are establishing and keeping alive the communications link for the duration of the session, keeping the communication secure, synchronizing the dialogue between the two nodes, determining whether communications have been cut off, and, if so, figuring out where to restart transmission, and terminating communications. Session layer services also set the terms of communication by deciding which node communicates first and how long a node can communicate. Finally, the Session layer monitors the identification of session participants, ensuring that only the authorized nodes can access the session.
When you initiate a connection with your ISP, for example, the Session layer services at your
ISP’s server and on your computer negotiate the connection. If your data cable accidentally falls out of the wall jack, Session layer protocols on your end will detect the loss of a connection and initiate attempts to reconnect. If they cannot reconnect after a certain period of time, they will close the session and inform your client software that communication has ended.
Transport Layer:
Protocols in the Transport layer accept data from the Session layer and manage end‑to‑end delivery of data. That means they can ensure that the data is transferred from point A to point B reliably, in the correct sequence, and without errors. Without Transport layer services, data could not be verified or interpreted by its recipient. Transport layer protocols also handle flow control, which is the process of gauging the appropriate rate of transmission based on how fast the recipient can accept data. Dozens of different Transport layer protocols exist, but most modern networks, such as the Internet, rely on only a few. In the example of retrieving a Web page, a Transport layer protocol called TCP (Transmission Control
Protocol) takes care of reliably transmitting the HTTP protocol’s request from client to server and vice versa.
Network Layer:
The primary function of protocols at the Network layer, the third layer in the OSI model, is to translate network addresses into their physical counterparts and decide how to route data from the sender to the receiver. Addressing is a system for assigning unique identification numbers to devices on a network. Each node has two types of addresses.
One type of address is called a network address. Network addresses follow a hierarchical addressing scheme and can be assigned through operating system software. They are hierarchical because they contain subsets of data that incrementally narrow down the location of
a node, just as your home address is hierarchical because it provides a country, state, ZIP code, city, street, house number, and person’s name. Network layer address formats differ depending on which Network layer protocol the network uses. Network addresses are also called network layer addresses, logical addresses, or virtual addresses. The second type of address assigned to each node is called a physical address,
Data Link Layer:
The primary function of protocols in the second layer of the OSI model, the Data Link layer, is to divide data they receive from the Network layer into distinct frames that can then be transmitted by the Physical layer. A frame is a structured package for moving data that includes not only the raw data, or “payload,” but also the senders and receiver’s network addresses, and error checking and control information. The addresses tell the network where to deliver the frame, whereas the error checking and control information ensure that the frame arrives without any problems.
Physical Layer:
The Physical layer is the lowest, or first, layer of the OSI model. Protocols at the Physical layer accept frames from the Data Link layer and generate signals as changes in voltage at the NIC. (Signals are made of electrical impulses that, when issued in a certain pattern, represent information.) When the network uses copper as its transmission medium, these signals are also issued over the wire as voltage. In the case of fiber optic cable, signals are issued as light pulses. When a network uses wireless transmission, the signals are sent from antennas as electromagnetic waves.
Don't Forget To Say THANKS !!!!